Through targeted acquisitions, massive investments in AI and the clever linking of cloud services with security solutions, the Group is conquering a market that was traditionally dominated by specialists. This development promises companies cost benefits and simplified management – but at the same time raises questions about dependencies and digital sovereignty.
The central question is: Are companies benefiting from Microsoft’s integrated security ecosystem or are new risks arising from the growing market concentration? An overview of strategy, market trends and practical challenges for IT decision-makers.
From software giant to security market leader
The figures speak for themselves: in 2023, Microsoft already generated annual revenue of 20 billion US dollars in the cybersecurity sector – double that of 2021. With annual growth of 18.6 percent, the Group is on course to overtake established market leaders such as Palo Alto Networks and Fortinet. In the first quarter of 2024 alone, Microsoft invested 20 billion US dollars in its technology infrastructure, with a focus on AI development and cloud capacities.
This impressive development is based on a systematic acquisition strategy that goes far beyond traditional software acquisitions. Microsoft has made targeted purchases of innovative security specialists and integrated their technologies into its growing ecosystem.
Strategic milestones: from Sybari to Miburo
The development of Microsoft’s security portfolio followed a clear plan. The acquisition of Sybari Software laid the foundation for corporate email security back in 2005. The acquisition of Aorato (2014) brought AI-based anomaly detection for Active Directory, while Adallom (2015) added cloud access security broker functions.
The acquisition of Hexadite (2017), whose automated incident response technology is now at the heart of Microsoft Defender and Sentinel, was particularly significant. CyberX (2020) expanded the portfolio to include industrial IoT security, RiskIQ (2021) strengthened external threat detection, and ReFirm Labs (2021) added firmware security expertise.
The recent acquisition of Miburo (2022) shows Microsoft’s foresight: The company specializes in the analysis of disinformation and social engineering attacks – a threat area that is rapidly gaining relevance due to AI-generated content.
These acquisitions have been seamlessly integrated into Microsoft’s core platforms. Microsoft Defender, Sentinel and Entra ID now form a coherent security ecosystem that covers all key areas from endpoint security to identity management and cloud security.
The integrated security ecosystem: advantages for companies
Microsoft’s success is based on a fundamental paradigm shift in IT security. Instead of isolated security tools, the company offers an end-to-end integrated platform that promises considerable practical benefits.
The economic argument is convincing: by bundling different security services, companies can save on high acquisition, maintenance and license costs for separate special solutions. Medium-sized companies in particular benefit from not having to invest in a patchwork of different security tools. A central management interface reduces complexity and sources of error, while the deep integration between the components enables more efficient threat detection.
The platform is technically impressive thanks to its networking: Microsoft Defender for Endpoint communicates seamlessly with Sentinel, the cloud-native SIEM system, while Entra ID enables granular access control across all applications. Microsoft Purview complements the ecosystem with data classification and compliance management. This integration promises what isolated security solutions are often unable to deliver: a holistic overview of the threat situation.
The strategy is paying off: According to The Business Research Company, the global cybersecurity market will grow to 267.5 billion US dollars (2025) and is set to rise to 434.8 billion US dollars by 2029. With a doubling to 68.5 billion US dollars, cloud security is the fastest growing segment – precisely where Microsoft can play to its strengths.
The limits of integration: heterogeneous IT reality
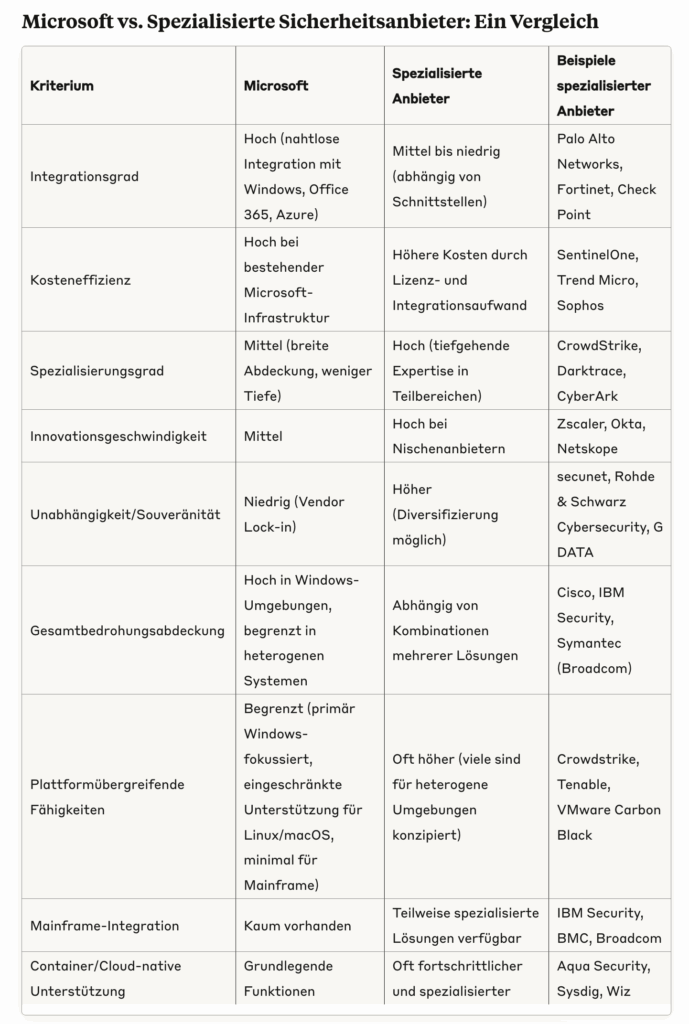
However, Microsoft’s success story has a crucial catch: the strong focus on Windows environments meets the reality of heterogeneous IT landscapes. In addition to Windows, many companies also operate mainframe systems, Linux servers and macOS workstations – a diversity that poses considerable challenges for Microsoft’s integrated security strategy.
Microsoft Defender for Endpoint offers basic support for macOS and Linux, but with a significantly reduced range of functions. There are practically no native integrations for mainframe systems such as IBM z/OS. The deep operating system integration that Microsoft enables with Windows remains technically and licensing-wise limited on third-party platforms.
These limitations have practical consequences: Although Microsoft Sentinel can record logs from different systems, it offers significantly fewer predefined detection rules for non-Microsoft environments. In landscapes without Active Directory or with parallel directory services, integration gaps arise that undermine the promise of a uniform security platform.
Specialized providers have recognized this gap in the market. Crowdstrike, SentinelOne and Trend Micro design their solutions from the ground up for heterogeneous environments and offer comparable functions for Windows, macOS and Linux. In the mainframe sector, specialists such as BMC, Broadcom or IBM itself continue to dominate with dedicated z/OS security solutions.
The limitations of the Microsoft platform are particularly evident in the growing container and cloud-native segment. Specialized providers such as Aqua Security, Sysdig or Wiz offer more advanced container security solutions, while tools such as Snyk or BlackDuck are leaders in the monitoring of open source components.
Market dynamics: consolidation meets specialization
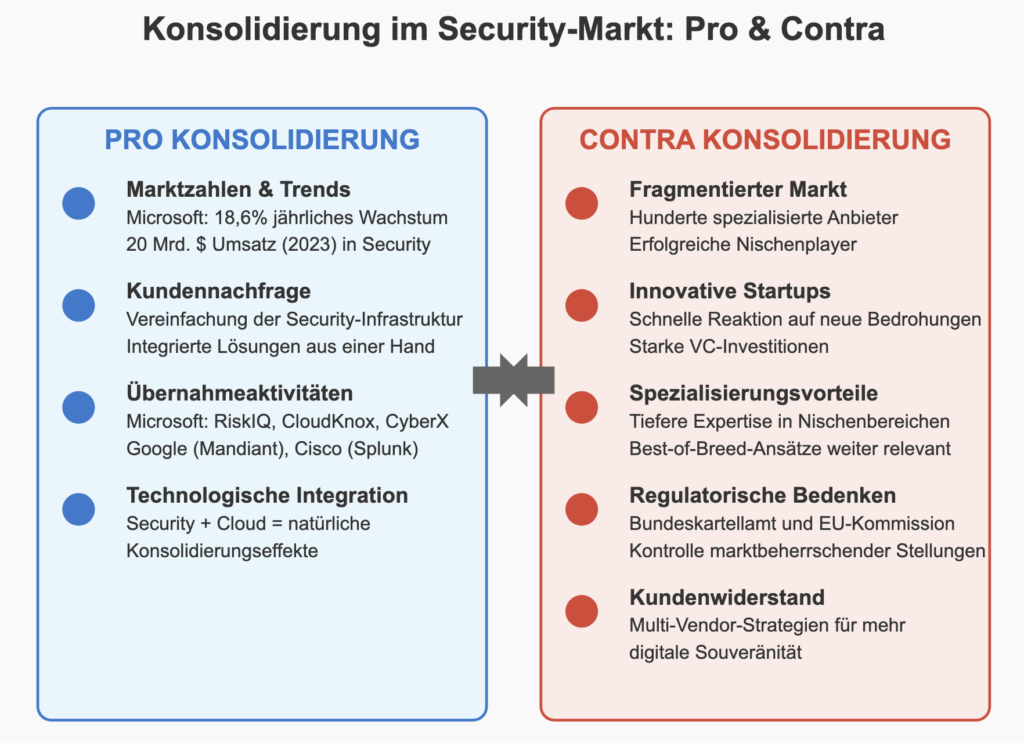
The cybersecurity industry finds itself in a fascinating field of tension. While Microsoft and other tech giants are focusing on consolidation, new specialized threats are constantly emerging that require innovative solutions. This dichotomy is shaping the entire development of the industry.
Historically, the IT industry has shown cyclical patterns: phases of consolidation alternate with periods of fragmentation. In the 1980s, closed systems from large manufacturers dominated, before open standards ushered in an era of specialization. The 2000s brought consolidation again through enterprise suites. Today, we are experiencing a new wave of consolidation with cloud-based security platforms.
The fact that neither all-in-one approaches nor best-of-breed strategies have been able to establish themselves in the long term reflects fundamental market mechanisms. Specialized providers react faster to new threats and develop innovative solutions, while platform providers reduce complexity and cut costs. This dynamic explains why, despite Microsoft’s success, there are still hundreds of specialized security providers on the market.
Current takeover activity shows the ongoing trend towards consolidation: in addition to Microsoft’s acquisitions, Google took over Mandiant for 5.4 billion dollars, while Cisco acquired Splunk for 28 billion dollars. At the same time, the venture capital market continues to invest heavily in security start-ups that address new threats such as AI-based attacks or quantum computing risks.
Pragmatic hybrid strategies as a solution
In view of these market dynamics, orchestrated multi-vendor strategies are increasingly becoming a viable solution. Modern Security Orchestration, Automation and Response (SOAR) platforms enable the centralized management of heterogeneous security environments. In addition to Microsoft Sentinel, platform-independent solutions such as Splunk Enterprise Security or IBM Security QRadar SOAR offer standardized interfaces to various security tools across all operating systems.
A future-proof approach for companies could lie in a deliberate layered model: platform-specific basic protection through optimal solutions for each environment, supplemented by cross-platform tools for overarching functions such as vulnerability management or network detection and response. Centralized orchestration through vendor-neutral SIEM/SOAR systems enables uniform monitoring and response.
Risks of consolidation: what is at stake
The growing dominance of a few large providers harbors considerable risks that must be taken into account when making strategic security decisions. The SolarWinds hack impressively demonstrated that even highly integrated platforms are not immune to large-scale attacks – especially as vulnerabilities in Azure Active Directory were also affected.
The consolidation of sensitive data in a single platform creates attractive targets for cyberattacks. If attackers were to exploit vulnerabilities in Microsoft’s infrastructure, huge amounts of data could be compromised. At the same time, centralized data storage requires sophisticated authorization systems to meet data protection requirements – a particular challenge for highly regulated industries.
The legacy problem further exacerbates these risks. Despite continuous modernization, Microsoft continues to struggle with vulnerabilities in old components. According to The Hacker News, 1,360 Microsoft vulnerabilities were disclosed in 2024, including critical vulnerabilities in Windows and Edge. These figures make it clear that consolidation strategies can harbor new risks, especially if outdated technologies continue to be used.
In the long term, there is a threat of standardization across the entire security industry, which could limit its ability to innovate. Start-ups in the field of AI-based security applications could find it difficult to compete against established platform providers. This is particularly critical in the case of emerging threats that require fast and innovative responses.
Technological trends
What users should always keep an eye on are the trends. And they look like this: https://www.splashtop.com/blog/cybersecurity-trends-2025
- Artificial intelligence: AI-based systems will be crucial for detecting and defending against cyber attacks in 2025. They enable proactive threat analysis and automated incident response.
- Zero trust architectures: More and more companies are relying on zero trust to granularly control access and minimize attack surfaces – particularly relevant in hybrid and remote work environments.
- Supply chain security: attacks on supply chains are on the rise, which is why companies are investing more in securing third-party access
Digital sovereignty: the European perspective
European companies and authorities are increasingly faced with the question of digital sovereignty. Microsoft’s 700 million dollar deal with Poland has already sparked debates about its dependence on US technology companies. Experts are increasingly calling for EU-based alternatives in order to retain control over critical infrastructures.
These concerns are not unfounded. Kai Wawrzinek from Impossible Cloud Network puts it in a nutshell: “It is a national security risk if Europe’s cybersecurity systems increasingly run on the cloud systems of US companies.”
The question of technological independence is becoming increasingly urgent, especially for critical infrastructures and public authorities.
Recommendations for IT decision-makers
The complexity of the topic requires a differentiated approach. Companies should develop their security strategy on three levels: the technical evaluation of their IT landscape, strategic risk assessment and long-term flexibility.
From a technical perspective, IT managers must honestly assess how homogeneous their environment actually is. In Windows-dominated landscapes, integrated Microsoft solutions can offer considerable advantages. In heterogeneous environments with significant proportions of Linux, macOS or mainframe systems, cross-platform strategies should be preferred.
Strategically, it is important to find the balance between efficiency and dependency. David Branscome from Microsoft sums it up aptly: “Vendor consolidation is not a one-size-fits-all solution; it requires careful planning, implementation and a continuous review process to meet the specific needs of an organization.”
In the long term, companies should focus on flexibility. APIs and open standards make it possible to benefit from the advantages of integrated platforms without becoming completely dependent on one provider. Security orchestration is becoming the key technology for centrally managing and coordinating different security solutions.
Conclusion: The future lies in intelligent orchestration
Microsoft is undoubtedly on its way to becoming a dominant force in the cybersecurity market. The massive focus on AI-based solutions and the continuous expansion of the portfolio show the will to further expand this influence. However, the limits of this influence are determined by the heterogeneous reality of modern IT landscapes and the ongoing innovation dynamics of specialized providers.
The historical cycles of the IT industry suggest that neither all-in-one nor best-of-breed will dominate in the long term. The future of IT security probably lies in intelligently orchestrated multi-platform security architectures that combine the best of both worlds. The trend towards hybrid and multi-cloud is reinforcing this development: companies that use AWS, Azure and Google Cloud in parallel will inevitably need cross-platform security concepts.
For IT decision-makers, this means a multi-layered trade-off between cost efficiency, technical coverage and strategic independence. The key lies not in the dogmatic pursuit of a single strategy, but in the intelligent combination of different approaches – adapted to the specific requirements and circumstances of the respective company.
The cybersecurity industry will need to continue to find a balance between consolidation and innovation. Microsoft’s success will motivate other large technology companies to adopt similar strategies, while at the same time new threats will spawn innovative startups. Understanding and strategically leveraging these dynamics will be critical for organizations to future-proof their IT security.






