Meta has introduced a new feature called “Friend Map” on Instagram, which allows users to see the location of their friends and discover common meeting points. However, what is advertised as an entertaining social media function is causing considerable concern among security experts at Check Point.
The Friend Map collects location data through two methods. First, it creates app-controlled location logs that record the user’s last location when the Instagram app is opened. Second, the function indexes all reels, stories, or feed posts with location tags and links them to the user profile.
Although this is not a continuous GPS tracking system, repeated logins at the same coordinates create a time-stamped movement history. This allows for precise conclusions to be drawn about home and work addresses, travel habits, and frequently visited places.
Centralized storage without end-to-end encryption
The collected location data is stored centrally on Meta servers—part of the same infrastructure that operates Facebook and Messenger. Meta does not specify exactly how long this data is stored, using the vague phrase “as long as necessary” for services, analytics, and commercial purposes. Unlike security-oriented location services, this information is not encrypted end-to-end.

This centralization makes the data an attractive target for cybercriminals. In the event of a security breach, attackers could steal not only user data but also detailed movement profiles of millions of users. Additionally, integration into Meta’s advertising ecosystem enables precise targeting—but the same technology can be misused for malicious purposes.
Physical and digital threats
The risks fall into two categories: physical and digital dangers. On a physical level, location disclosure can lead to stalking, harassment, or unwanted personal contact. Attackers can recognize movement patterns and use them for planned encounters. Criminals also use location tags to plan break-ins when residents are demonstrably away from home.
In the digital realm, location data becomes a profiling tool. Meta can link this information with browsing history, purchase data, and demographic information, creating opportunities for targeted disinformation, fraud, and phishing. Cybercriminals can derive political beliefs or health conditions from location patterns and create manipulative content tailored to individual users.
Comparison with Apple and Snapchat
Compared to Apple’s Find My feature, which uses end-to-end encryption and is designed solely for security purposes, or Snapchat’s Snap Map, Instagram’s Friend Map differs in three key ways: its integration into Meta’s broader ecosystem, the commercial incentive to collect data within an ad-supported platform, and Meta’s history of data breaches in recent years.
Underground activities already observable
Threat analysts have observed discussions in underground forums about reverse engineering the Instagram API and methods for collecting large amounts of user coordinates just days after the feature was introduced. These activities mirror known attack patterns from previous incidents, such as the Strava heatmap leak that inadvertently exposed military assets.
Protective measures for users
Check Point recommends several protective measures:
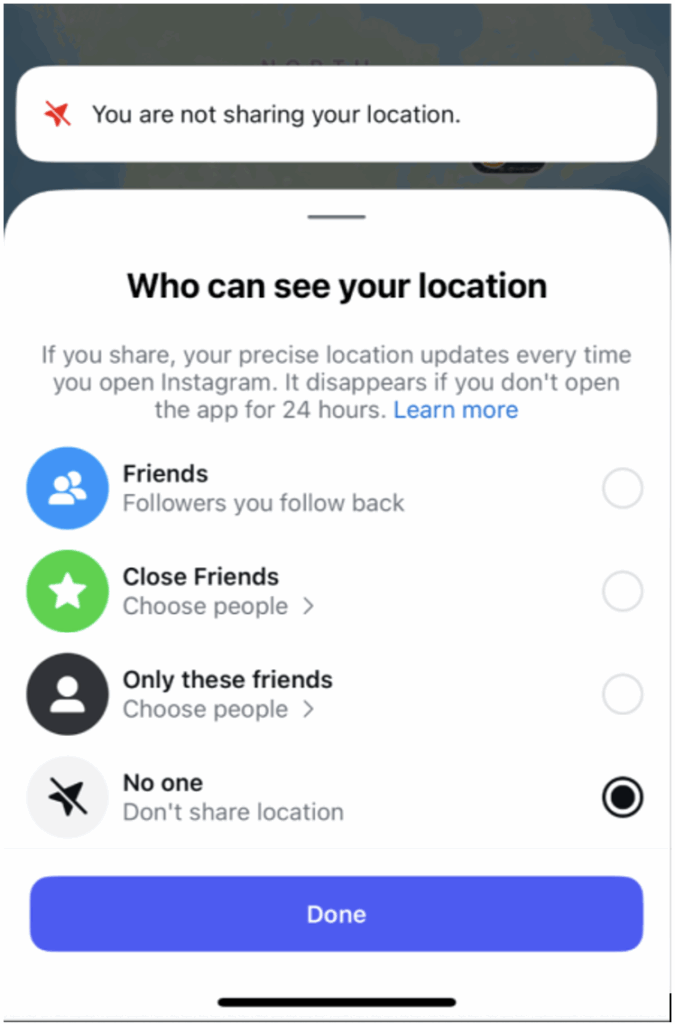
- Set location sharing to “No one” under “Messages → Map → Settings”
- In smartphone privacy settings, restrict location access for Instagram to “While using the app” or deactivate it completely
- Regularly review your follower list and remove unknown people
- Parents can use Instagram’s family section to monitor their children’s location settings
- If location sharing is temporarily activated, deactivate it immediately afterward
By implementing these measures, users can better protect themselves from the potential risks associated with Instagram’s Friend Map feature while still enjoying the platform’s other functionalities.
(lb/CheckPoint)


