The infamous Trojan from 2019 is once again making headlines. Security researchers from ESET have discovered that AsyncRAT is now even more dangerous and has spread much more widely thanks to new variants.
AsyncRAT: New generation of digital espionage
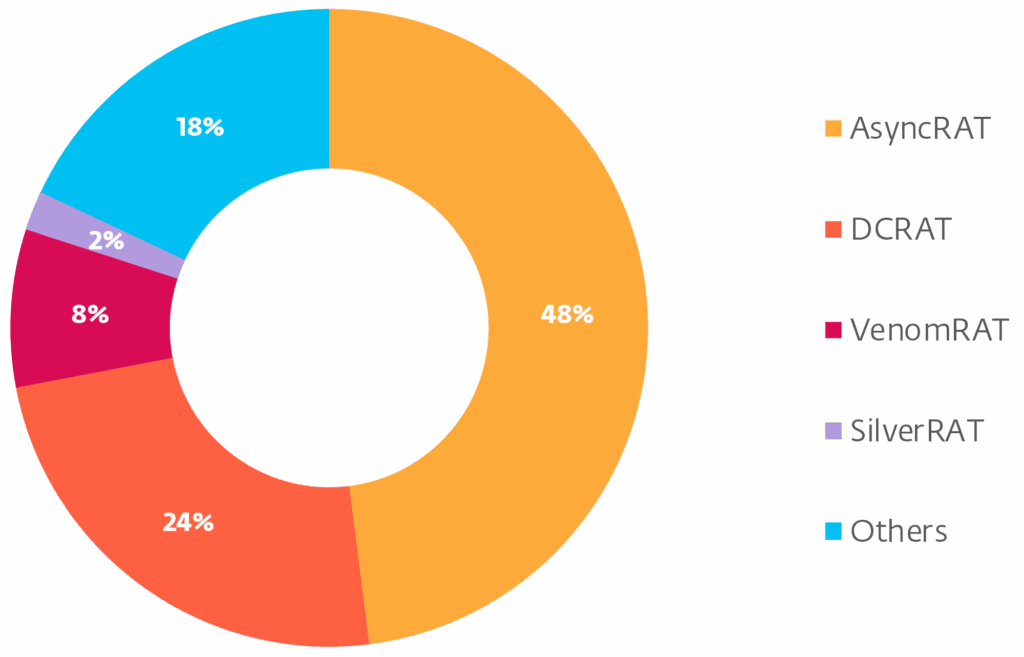
AsyncRAT has been one of the most feared remote control Trojans on the Internet for years. Now an analysis by the European IT security company ESET shows just how much the tool has evolved. The current investigation reveals that there are now several new offshoots of the malware that differ significantly from the original in terms of functionality. At the same time, the tool has been adapted in such a way that it can now also be used by less technically skilled attackers.
Technically more sophisticated and harder to detect
The experts particularly emphasize the modular structure and the improved camouflage mechanisms of the new variants. This makes it difficult for modern security systems to detect the malware. Because the tool can be easily extended, numerous forks have been created. These are each aimed at different purposes and attack strategies.
DcRat & VenomRAT: Two of the most dangerous offshoots
According to ESET, the most widespread variants include the DcRat and VenomRAT Trojans. DcRat uses advanced methods to bypass security systems such as Microsoft’s Anti-Malware Scanning Interface (AMSI). In addition, it contains audio and video surveillance functions, can execute ransomware and offers a module that serves to amuse the attackers. It can be used to move the mouse pointer or switch off the victim’s screen.
Although VenomRAT is based on DcRat, it is considered an independent development. Due to similar configurations and a related structure, the researchers nevertheless classify it as part of the AsyncRAT ecosystem.
BoratRAT & SantaRAT: Trojans with black humor
Some forks seem almost humorous at first glance. SantaRAT, for example, pretends to want to attack Santa’s laptop. BoratRAT bears the name of a well-known film character and plays with his image. However, despite this ironic packaging, both are fully functional Trojans that have already been used in real attacks.

NonEuclidRAT & JasonRAT: When malware gets scary
The offshoot NonEuclidRAT is particularly conspicuous. This malicious program contains plugins that can guess passwords using brute force attacks, spread via USB sticks and manipulate the clipboard. For example, crypto wallet addresses are automatically replaced. The Trojan also has a plugin that plays scary images and audio files to frighten victims.
Even more bizarre is JasonRAT, which works with variable names that are based on satanic symbols. The configuration data is available in Morse code, which makes decryption even more difficult. This approach shows how creative hackers can be in disguising their tools.
What are RATs anyway?
Remote access Trojans, or RATs for short, are programs that enable attackers to gain undetected access to other people’s computers. Once a system is infected, it can be extensively controlled remotely. The attackers can then steal data, access passwords, delete files, activate the camera or record keystrokes. These programs often gain access to their victims’ computers via fake websites or malicious email attachments.
Conclusion
The new variants of AsyncRAT show how rapidly digital threats are evolving. The spectrum ranges from technically sophisticated to disturbingly creative. But no matter how the Trojans are structured, they all have one goal: to gain control of other people’s systems and cause damage.
“The widespread availability of frameworks such as AsyncRAT significantly lowers the barrier to entry for aspiring cybercriminals and allows even novices to deploy sophisticated malware with minimal effort. This development further accelerates the creation and customization of malicious tools. This development underlines the importance of proactive detection strategies and in-depth behavioral analysis to effectively counter emerging threats,” summarizes Knežević.
Further information on AsyncRAT and its forks can be found in the new blog post on Welivesecurity.com.
(vp/ESET Deutschland GmbH)

